Essential Eight Compliance Without External Consultants
In a landscape where cyber threats evolve rapidly, organisations need a strong cyber security baseline like the Essential Eight to protect their data and infrastructure. However, understanding exactly what needs to be done can be overwhelming, even for seasoned IT professionals. E8Assessment eliminates the confusion and cuts through the complexity by providing clear, actionable steps that your internal IT team can follow—without spending thousands on consultants.
Start Assessment NowStruggling with Essential Eight Compliance?
Over-estimation of Maturity Levels
Many organisations over-estimate their maturity levels during self-assessments, leading to a false sense of security. Research by the Office of the Auditor General WA revealed that several entities believed they had achieved higher maturity levels than they had, leaving them with an inadequate implementation and further vulnerability to cyberattacks.
Time and Resource Constraints
Achieving compliance requires significant time and resources. Internal IT teams are often too overwhelmed with BAU and other priorities, and do not have the time to research and understand the detailed requirements, leading to the need for costly external consultants.
Cost of External Consultants
External consultants are often engaged to navigate Essential Eight complexities, which can be costly and slow down adoption, particularly for smaller businesses.
Complexity of Implementation
Implementing the Essential Eight can be technically challenging, especially with controls like patch management, application whitelisting, and MFA. This can often lead to operational disruptions adding further time and cost during implementation.
Adapting to Evolving Threats
Cyber threats constantly evolve, and the Essential Eight framework itself undergoes periodic updates to address the changing threat landscape. Organisations must continuously reassess their security posture, which adds to the complexity and workload.

Application control

Patch Applications

Restrict Microsoft Office

User Application Hardening
Attack Prevention Strategies

Restrict Admin Privileges

Patch Operating Systems

Multi-Factor Authentication
Limit Extent of Attack

Regular Backups
Recover
How does E8Assessment Solve
These Challenges


Accurate Self-Assessment
E8Assessment guides your IT Team through a structured self-assessment to accurately determine your organisation's maturity levels for each of the Essential Eight controls. This reduces the risk of overestimating your current state and ensures a more realistic picture of your security posture.

Detailed Explanations
Throughout the self-assessment, and further detailed within the report, your team will be made aware of what is required to achieve each of the controls within the Essential Eight. No need to spend hours or days researching online.

Reduce Your Consultant Costs
Your IT Team already understands your environment. By providing them with a step-by-step assessment and actionable report with implementation technical resources, E8Assessment eliminates the need for expensive consultants. Internal IT teams can take charge of the compliance process, significantly reducing costs.

Real-World Examples
During the self-assessment, you are provided with real-world examples and scenarios to help you relate the framework requirements back to your organisation. This helps to maximise the accuracy of your self-assessment, and prompts you to consider parts of your environment you may not have considered, such as “Shadow IT”.

Adapting to Updates
E8Assessment is regularly updated to reflect changes in the Essential Eight framework, and as new technologies are available to help meet compliance. This ensures that your organisation is working with the latest guidance, helping them stay ahead of evolving threats

Actionable Reports
Tailored reports provide clear, step-by-step actions, eliminating guesswork and ensuring teams know exactly what to do next to improve your security posture.
How it works

Answer


Report


Implement


Reassess
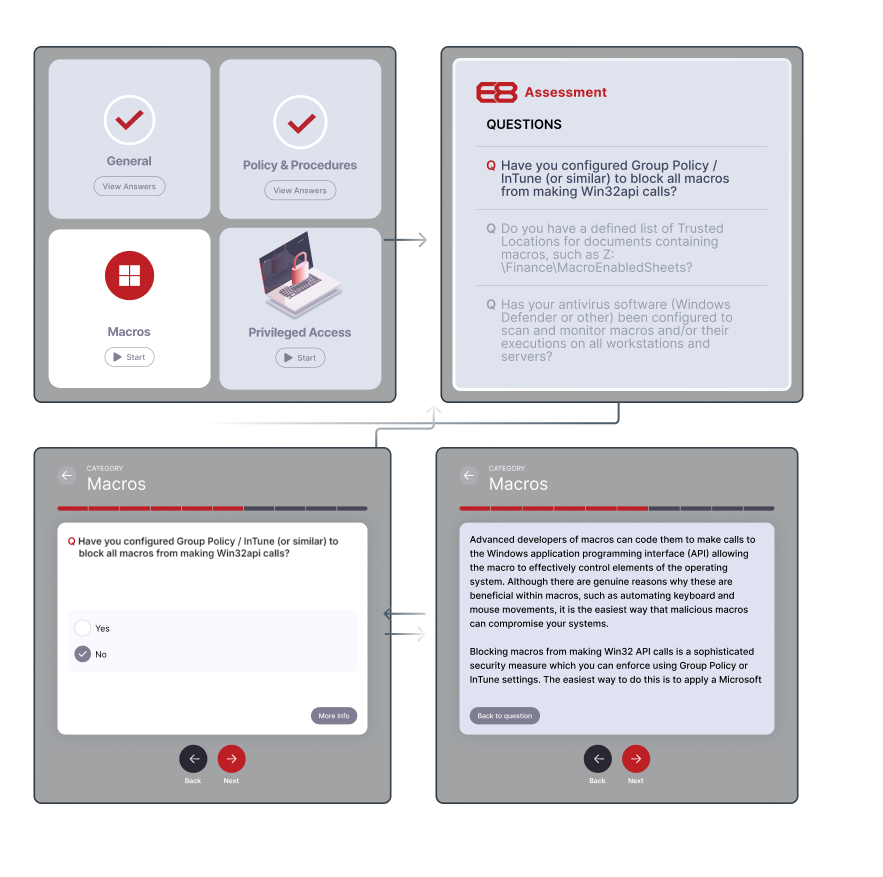
E8Assessment is an online, self-paced multiple-choice questionnaire specifically designed to assess your organisation’s maturity level. You will then receive a tailored report that not only documents your maturity level, but also provides you with technical resources to help you implement your specific compliance gaps.
Answer
Your IT Team answer questions about your environment. All questions are in “Plain IT English” with real-world examples to help you answer - No ambiguous cyber-speak!
Report
A report is compiled by our cyber experts specifically for you, documenting your maturity level against the controls, and specifically where you have gaps against each control.
Implement
Using the ASD process guidelines and years of hands-on implementation expertise, we have compiled technical guides and videos to help you implement the controls. These are available within your tailored report, providing you with the expertise you need to implement your specific compliance gaps.
Reassess
Check back in at least annually and reassess your environment to monitor your cyber journey.
No software installation or running of scripts required!
To further illustrate how E8Assessment works, watch our introductory video.

Key Benefits

ASD / ACSC Aligned
The questionnaire has been specifically designed to align with ASD Essential Eight requirements, while making it easy for you to accurately answer the questions. The compiled report is also aligned to the ASD Essential Eight report standard.

Built for IT Professionals
We speak your language, with technical insights and real-world scenarios that make the Essential Eight easy to implement. We call it “Plain IT English”

Simple
We've made it so all of your IT Professionals can assess your maturity, and implement the required controls.

Affordable
Consultants will charge thousands for an assessment, so they can gather the information from your team. With E8Assessment, you can cut out the consultant middle-man with a DIY assessment and implementation by your IT team!

Actionable
Your report, which is tailored based on your answers, will not only tell you maturity level, but also specifically tell you where and how you need to improve.

Shareable Report
Our reports can be shared with your executive team, or third-parties to show where you are on your cyber journey.
Empower your IT team today. Start your E8Assessment journey now and enhance your cyber security posture with confidence.
Be your own expert
Whether you are a CISO, CTO, IT Manager, Cyber / Infra / Apps / Helpdesk Engineer, this is the simplest and cheapest way to assess where you are and what you need to with Essential Eight.
We have ensured that anyone working in IT can answer the questions, and understand the report! We call it “Plain IT English”.
Start Assessment